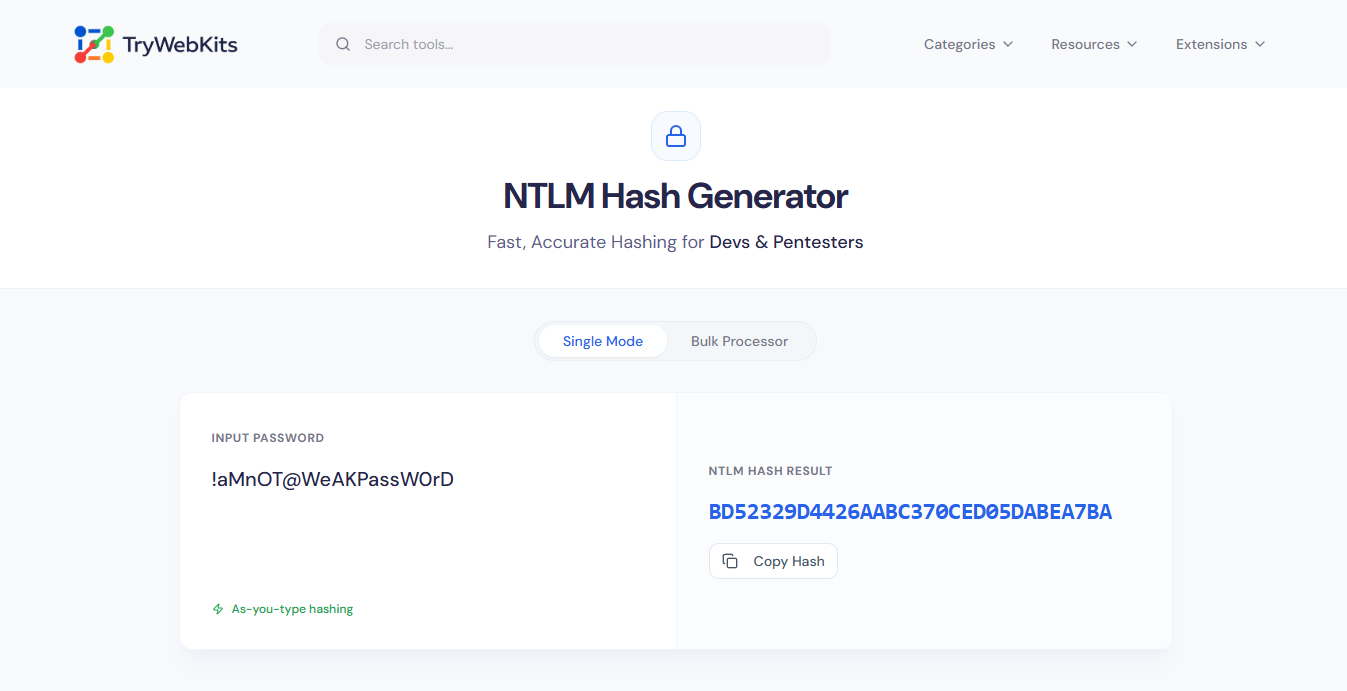
NTLM Hash Generator
Fast, Accurate Hashing for Devs & Pentesters
What Is NTLM Hash?
NTLM (New Technology LAN Manager) is a suite of Microsoft security protocols intended to provide authentication, integrity, and confidentiality to users. While modern systems often prefer Kerberos, NTLM remains widely used for backward compatibility in legacy Windows systems and specific network configurations.
Understanding NTLM Hash Generation
An NTLM hash generator converts plain text strings or passwords into a fixed-length hexadecimal string using the MD4 message-digest algorithm. This tool serves developers, system administrators, and penetration testers who need to verify credentials, test system interoperability, or conduct security auditing without setting up a full Windows server environment.
The process creates a standard 32-character string important for various authentication protocols.
How to Generate an NTLM Hash?
The process for creating an NTLM hash is streamlined for immediate results.
- 1
Input Data: Type the plain text password directly into the main input field.
- 2
Instant Conversion: View the generated hash immediately in the output box without clicking buttons.
- 3
Bulk Processing: Select the 'Bulk Processor' tab to process multiple passwords simultaneously.
- 4
Line-by-Line Entry: Paste a list of passwords, separated by new lines, into the bulk text area.
- 5
Copy Results: Retrieve the converted hashes from the output field for immediate use.
Core Functionalities
From one password to one thousand. Instant results either way
Instant Conversion
Hash generates immediately while typing, zero delay, no submit button required.
Bulk Processing
Processes large lists of passwords simultaneously within the dedicated bulk output tab interface.
Client-Side Security
Performs all hashing locally within the browser, ensuring sensitive data never leaves the device.
Cross-Platform
Works on desktop, tablet, and mobile devices with any modern browser.
Lightweight Architecture
Loads quickly even on slow connections, optimized for performance and minimal resource usage.
Standardized Output
Produces accurate, industry-standard 32-character hexadecimal strings compatible with all NTLM-supported systems.
Practical Usage Scenarios
This NTLM hash generator is used in several professional contexts
Legacy Integration
Generate valid NTLM hashes when testing authentication against older Windows servers that lack modern protocol support.
Penetration Testing
Create hashes for pass-the-hash attack simulations or verify captured credentials during authorized security audits.
Database Migration
Confirm imported password hashes match original plain text values without forcing user password resets.
Educational Research
Study how input variations produce unique hash outputs when learning cryptography and Windows authentication protocols.
Application Debugging
Reproduce authentication failures by generating known hash values to isolate code issues in development environments.
Compliance Verification
Test if password policies generate expected NTLM hashes during regulatory audit preparations.
Closing the Door on Net-NTLMv1
Net-NTLMv1 relies on weak DES encryption. Attackers use "Rainbow Tables”,massive datasets of pre-computed keys, to reverse the encryption almost instantly.
The Vulnerability
Net-NTLMv1 relies on weak DES encryption. Attackers use "Rainbow Tables" to reverse encryption instantly.
The Attack
By forcing a server to use a specific challenge code (often 1122334455667788), an intruder can capture the response and use these tables to steal credentials.
The Solution
Organizations must disable Net-NTLMv1. Security standards now mandate using NTLMv2 or, preferably, Kerberos for all network authentication to prevent rapid "Pass-the-Hash" attacks.
Reference
Net-NTLMv1 Deprecation & Rainbow Tables
Read the full technical analysis by Google Cloud and Mandiant on why Net-NTLMv1 is now considered obsolete and how attackers use consumer-grade hardware to recover passwords.
Frequently Asked Questions (FAQ’s)
Yes, the NTLM protocol is case-sensitive. Changing a single letter from uppercase to lowercase will result in a completely different hash output.
No, NTLM is a one-way function. It is designed to be irreversible, though weak passwords can potentially be cracked using rainbow tables or brute force.
No. LM (LAN Manager) is an older, less secure protocol. NTLM uses the MD4 algorithm and supports longer passwords with case sensitivity, unlike LM.
Browser performance generally dictates the limit, but the tool comfortably handles hundreds of lines of text for bulk conversion tasks without slowdown.
No, standard NTLM (v1) hashes are not salted. The same password will always produce the identical hash string, making it deterministic.